Hello Everyone! We are back with another interesting post on Solr. One of the crucial requirements while setting up a solr application is to provide selective access to various resources allocated on the solr instance. Put simply, we need a mechanism to handle who logs in to the server and no unintended party gets access to various resources. When planning how to secure Solr, one should consider which of the available features or approaches are right for them.
There are following ways to authenticate the users:
- Kerberos Authentication Plugin:
- If you are using Kerberos to secure your network environment, the Kerberos authentication plugin can be used to secure a Solr cluster. This allows Solr to use a Kerberos service principal and keytab file to authenticate with ZooKeeper and between nodes of the Solr cluster (if applicable). Users of the Admin UI and all clients would also need to have a valid ticket before being able to use the UI or send requests to Solr.
- When setting up Solr to use Kerberos, configurations are put in place for Solr to use a service principal, or a Kerberos username, which is registered with the Key Distribution Center (KDC) to authenticate requests. The configurations define the service principal name and the location of the keytab file that contains the credentials.
- The Solr authentication model uses a file called
security.json. If this file is created after an initial startup of Solr, a restart of each node of the system is required. -
Service Principals and Keytab Files
Each Solr node must have a service principal registered with the Key Distribution Center (KDC). The Kerberos plugin uses SPNego to negotiate authentication.
Using
HTTP/host1@YOUR-DOMAIN.ORG, as an example of a service principal:HTTPindicates the type of requests which this service principal will be used to authenticate. TheHTTP/in the service principal is a must for SPNego to work with requests to Solr over HTTP.host1is the hostname of the machine hosting the Solr node.YOUR-DOMAIN.ORGis the organization-wide Kerberos realm.
Multiple Solr nodes on the same host may have the same service principal since the hostname is common to them all.
Along with the service principal, each Solr node needs a keytab file that should contain the credentials of the service principal used. A keytab file contains encrypted credentials to support passwordless logins while obtaining Kerberos tickets from the KDC. For each Solr node, the keytab file should be kept in a secure location and not shared with users of the cluster.
Since a Solr cluster requires internode communication, each node must also be able to make Kerberos enabled requests to other nodes. By default, Solr uses the same service principal and keytab as a ‘client principal’ for internode communication.
Kerberized ZooKeeper
When setting up a kerberized SolrCloud cluster, it is recommended to enable Kerberos security for ZooKeeper as well.
In such a setup, the client principal used to authenticate requests with ZooKeeper can be shared for internode communication as well. This has the benefit of not needing to renew the ticket granting tickets (TGTs) separately, since the ZooKeeper client used by Solr takes care of this. To achieve this, a single JAAS configuration (with the app name as Client) can be used for the Kerberos plugin as well as for the ZooKeeper client.
ZooKeeper Configuration
If you are using a ZooKeeper that has already been configured to use Kerberos, you can skip the ZooKeeper-related steps shown here.
Since ZooKeeper manages the communication between nodes in a SolrCloud cluster, it must also be able to authenticate with each node of the cluster. Configuration requires setting up a service principal for ZooKeeper, defining a JAAS configuration file and instructing ZooKeeper to use both of those items.
Create security.json
Create the
security.jsonfile.In SolrCloud mode, you can set up Solr to use the Kerberos plugin by uploading the
security.jsonto ZooKeeper while you create it, as follows: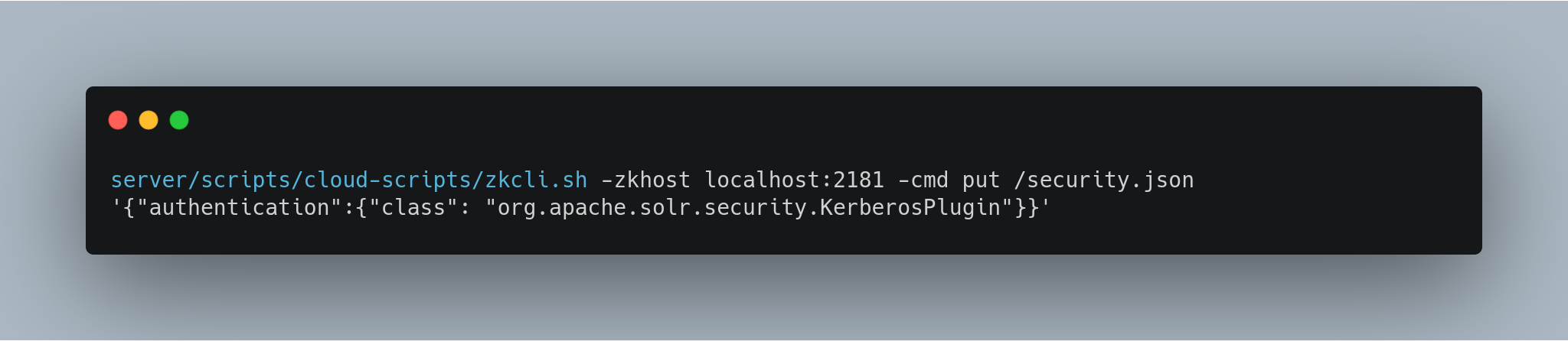
If you are using Solr in standalone mode, you need to create the
security.jsonfile and put it in your$SOLR_HOMEdirectory.Define a JAAS Configuration File
The JAAS configuration file defines the properties to use for authentication, such as the service principal and the location of the keytab file. Other properties can also be set to ensure ticket caching and other features.
The following example can be copied and modified slightly for your environment. The location of the file can be anywhere on the server, but it will be referenced when starting Solr so it must be readable on the filesystem. The JAAS file may contain multiple sections for different users, but each section must have a unique name so it can be uniquely referenced in each application.
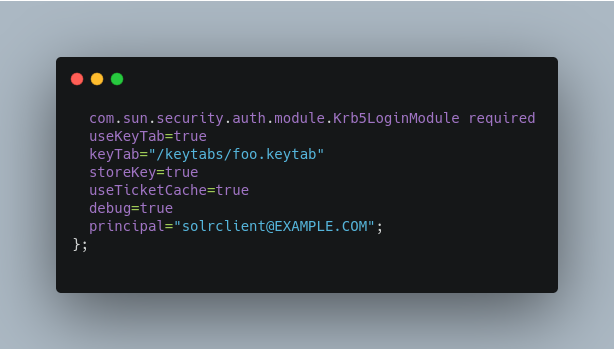
In the below example, we have created a JAAS configuration file with the name and path of
/home/foo/jaas-client.conf. We will use this name and path when we define the Solr start parameters in the next section. Note that the clientprincipalhere is the same as the service principal. This will be used to authenticate internode requests and requests to ZooKeeper. Make sure to use the correctprincipalhostname and thekeyTabfile path.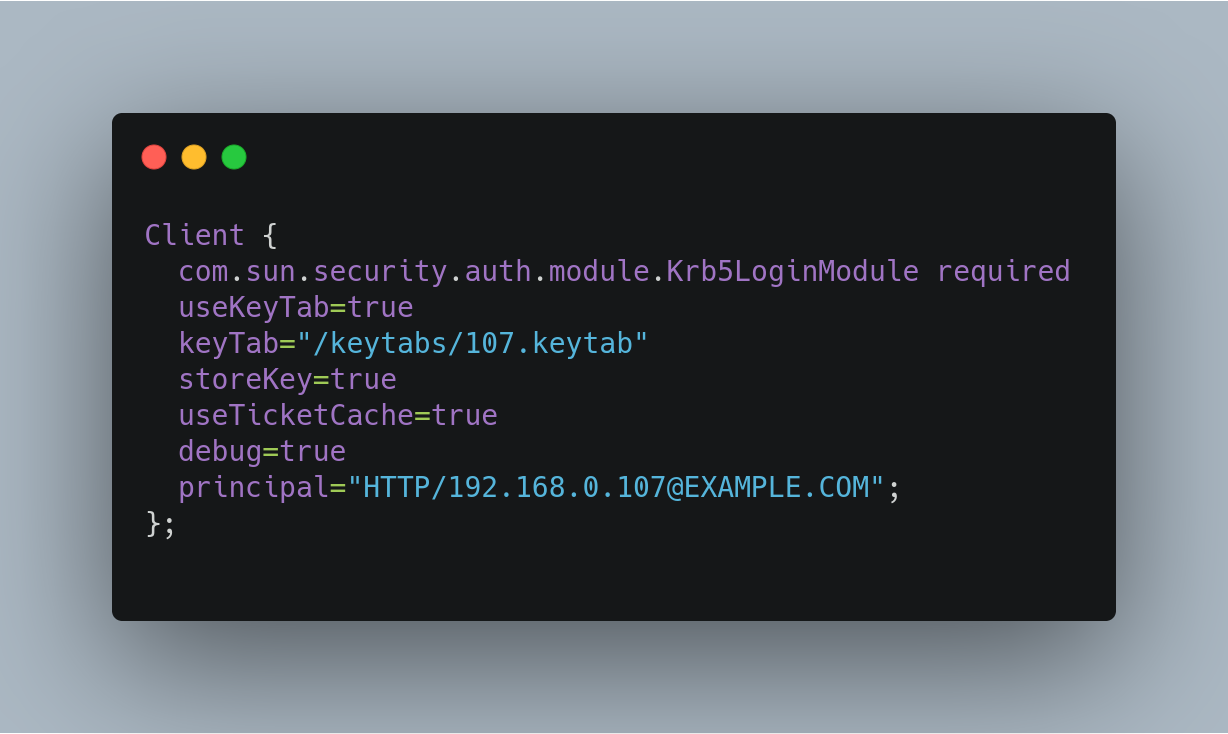
The first line of this file defines the section name, which will be used with the
solr.kerberos.jaas.appnameparameter, defined below.The main properties we are concerned with are the
keyTabandprincipalproperties, but there are others which may be required for your environment.For reference the ones in use in the above example are explained here:
useKeyTab: this boolean property defines if we should use a keytab file (true, in this case).keyTab: the location and name of the keytab file for the principal this section of the JAAS configuration file is for. The path should be enclosed in double-quotes.storeKey: this boolean property allows the key to be stored in the private credentials of the user.useTicketCache: this boolean property allows the ticket to be obtained from the ticket cache.debug: this boolean property will output debug messages for help in troubleshooting.principal: the name of the service principal to be used.
Solr Startup Parameters
While starting up Solr, the following host-specific parameters need to be passed. These parameters can be passed at the command line with the
bin/solrstart command or defined inbin/solr.in.shorbin/solr.in.cmdas appropriate for your operating system.solr.kerberos.name.rules- Used to map Kerberos principals to short names. Default value is
DEFAULT. Example of a name rule:RULE:[1:$1@$0](.*EXAMPLE.COM)s/@.*//. solr.kerberos.cookie.domain- Used to issue cookies and should have the hostname of the Solr node. This parameter is required.
solr.kerberos.cookie.portaware- When set to
true, cookies are differentiated based on host and port, as opposed to standard cookies which are not port aware. This should be set if more than one Solr node is hosted on the same host. The default isfalse. solr.kerberos.principal- The service principal. This parameter is required.
solr.kerberos.keytab- Keytab file path containing service principal credentials. This parameter is required.
solr.kerberos.jaas.appname- The app name (section name) within the JAAS configuration file which is required for internode communication. Default is
Client, which is used for ZooKeeper authentication as well. If different users are used for ZooKeeper and Solr, they will need to have separate sections in the JAAS configuration file. java.security.auth.login.config- Path to the JAAS configuration file for configuring a Solr client for internode communication. This parameter is required.
Here is an example that could be added to
bin/solr.in.sh. Make sure to change this example to use the right hostname and the keytab file path.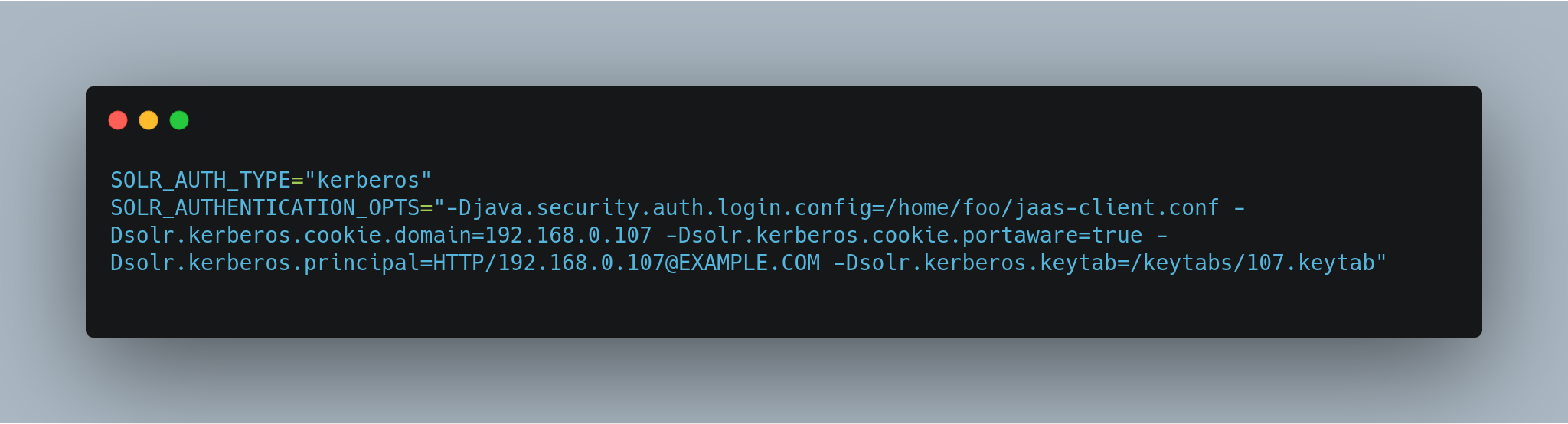
Using Delegation Tokens
The Kerberos plugin can be configured to use delegation tokens, which allow an application to reuse the authentication of an end-user or another application.
There are a few use cases for Solr where this might be helpful:
- Using distributed clients (such as MapReduce) where each client may not have access to the user’s credentials.
- When load on the Kerberos server is high. Delegation tokens can reduce the load because they do not access the server after the first request.
- If requests or permissions need to be delegated to another user.
To enable delegation tokens, several parameters must be defined. These parameters can be passed at the command line with the
bin/solrstart command.solr.kerberos.delegation.token.enabled- This is
falseby default, set totrueto enable delegation tokens. This parameter is required if you want to enable tokens. solr.kerberos.delegation.token.kind- The type of delegation tokens. By default this is
solr-dt. Likely this does not need to change. No other option is available at this time. solr.kerberos.delegation.token.validity- Time, in seconds, for which delegation tokens are valid. The default is 36000 seconds.
solr.kerberos.delegation.token.signer.secret.provider- Where delegation token information is stored internally. The default is
zookeeperwhich must be the location for delegation tokens to work across Solr servers (when running in SolrCloud mode). No other option is available at this time. solr.kerberos.delegation.token.signer.secret.provider.zookeper.path- The ZooKeeper path where the secret provider information is stored. This is in the form of the path + /security/token. The path can include the chroot or the chroot can be omitted if you are not using it. This example includes the chroot:
server1:9983,server2:9983,server3:9983/solr/security/token. solr.kerberos.delegation.token.secret.manager.znode.working.path- The ZooKeeper path where token information is stored. This is in the form of the path + /security/zkdtsm. The path can include the chroot or the chroot can be omitted if you are not using it. This example includes the chroot:
server1:9983,server2:9983,server3:9983/solr/security/zkdtsm.Start Solr
Once the configuration is complete, you can start Solr with the
bin/solrscript, as in the example below, which is for users in SolrCloud mode only. This example assumes you modifiedbin/solr.in.shorbin/solr.in.cmd, with the proper values, but if you did not, you would pass the system parameters along with the start command. Note you also need to customize the-zproperty as appropriate for the location of your ZooKeeper nodes.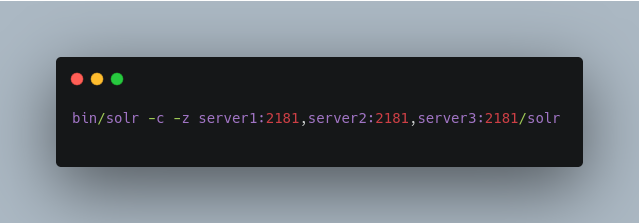
Using SolrJ with a Kerberized Solr
To use Kerberos authentication in a SolrJ application, you need the following two lines before you create a SolrClient:
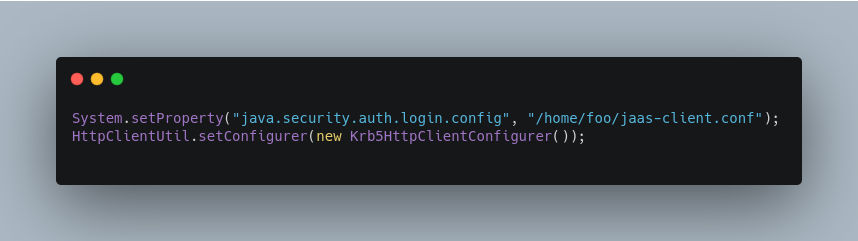
You need to specify a Kerberos service principal for the client and a corresponding keytab in the JAAS client configuration file above. This principle should be different from the service principal we created for Solr.
Delegation Tokens with SolrJ
Delegation tokens are also supported with SolrJ, in the following ways:
DelegationTokenRequestandDelegationTokenResponsecan be used to get, cancel, and renew delegation tokens.HttpSolrClient.Builderincludes awithDelegationTokenfunction for creating an HttpSolrClient that uses a delegation token to authenticate.
Sample code to get a delegation token:
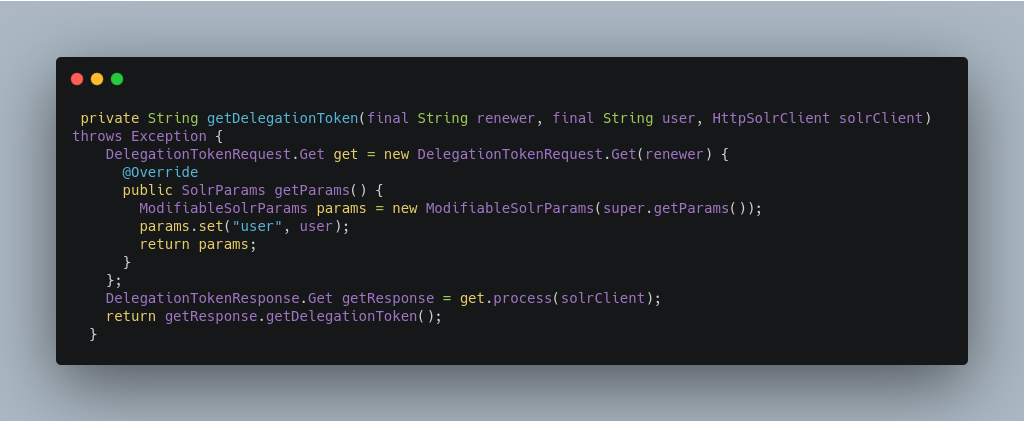
To create a
HttpSolrClientthat uses delegation tokens: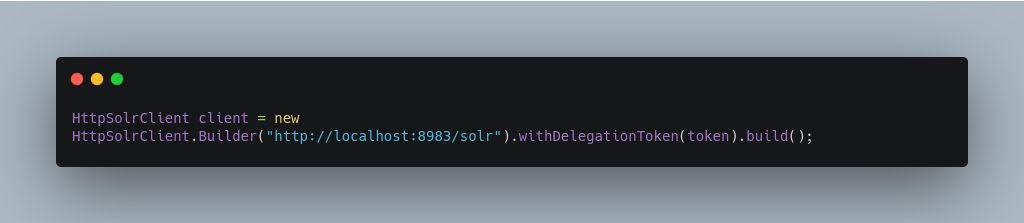
To create a
CloudSolrClientthat uses delegation tokens: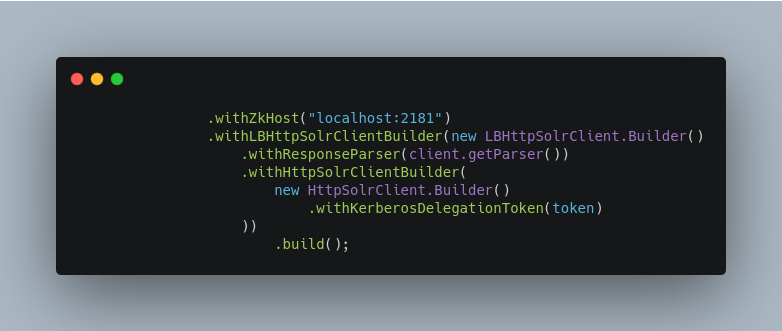
So, this is it about securing solr. We will be back with another post on solr very soon.
Manoj Kumar is a seasoned Digital Marketing Manager and passionate Tech Blogger with deep expertise in SEO, AI trends, and emerging digital technologies. He writes about innovative solutions that drive growth and transformation across industry.
Featured on – YOURSTORY | TECHSLING | ELEARNINGINDUSTRY | DATASCIENCECENTRAL | TIMESOFINDIA | MEDIUM | DATAFLOQ





